Tor Browser 1e2a62
- 11.5.2
- |
- Freeware
TOR, an acronym for The Onion Router, is not just another web browser. Its operation is based on a global computer network of servers (nodes), the list of which is public. These servers have a specific main function: to preserve the anonymity of s during a web browsing session (forum exchanges, history, anti-tracking, etc.). Not well known to the general public, it often appears in the news in Darknet-related cases, and for good reason, TOR allows access to the Dark Web and byes censorship.
Installation and familiarization of TOR Browser 2b544i
The TOR installer is classic. Its installation is only a matter of a few seconds. Nevertheless, it is clearly not the easiest browser for beginners to use. Fortunately, s can refer to the many materials and forums dedicated to the tool to facilitate their adaptation. To launch TOR, simply click on the “connect” button.

If you have already used the Firefox browser, you will notice that TOR is very similar to it. In fact, TOR is a very modified version of Firefox. As a result, it retains some of its features such as its design and some menus.

So you can customize the program interface by applying themes while creating your own toolbars to make it easier for you to use. However, due to privacy reasons, do not expect to have a Firefox Bis. You will notice that the program’s interface is very basic and consists of an address bar, a customizable toolbar and a menu.

Main features and performance 1p335v
As far as navigation is concerned, you will notice some slowness compared to a traditional browser. Indeed, your connection es through the network of the digital servers, which impacts the display of the pages and gives the impression of a slower connection than in normal times.
The browser s Firefox extensions. You can therefore take advantage of the huge catalogue of additional modules available. You will also notice that the software does not have a system. It is therefore not possible to synchronize TOR between its different devices.

Unlike traditional browsers, TOR allows by default to by censorship and other geographical restrictions. The browser is also the gateway to the Dark Web where there is a lot of illegal content, but that’s another story.
Navigation on sites on the TOR network is done through links with the extension .onion. Some of these sites are referenced on platforms such as Hidden Wiki or search engines such as Ahmia. It is impossible to access these sites using a normal browser such as Chrome or Firefox.
TOR Browser is not just a tool for accessing the Dark Web. It also provides access to an incredible amount of knowledge through university sites and other international scientific databases in.onion.
Finally, TOR can simply be used to preserve anonymity by asg a new IP address to the .
Is TOR secure enough? 2i522g
The is not lost and can use the software as a classic browser, but TOR is not a tool like any other. It allows the to manage almost any aspect of his or her privacy. Indeed, by clicking on the onion icon at the top left, the can “reset his identity” and adjust the security level.
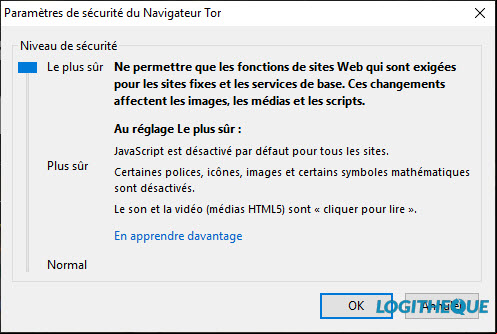
This slider allows you to disable certain web functions that can be hijacked to attack machine security or your anonymity. Among the web functions concerned are HTML5 and Javascript, which manage the display of certain content.
TOR is equipped by default with two extensions:
- HTTPS Everywhere which, as its name suggests, enables the HTTPS protocol on visited sites
- No script that allows you to disable Javascript and Flash in one click depending on the sites visited. No Script also allows you to block the exploitation of Spectrum and Meltdown vulnerabilities.
Thanks to the network of encrypted servers, TOR is able to hide your real IP address. Like a VPN, the browser will assign you another IP address, which is highly secure and is not vulnerable to the PSTN web flaw that allows s to be identified even when they use a VPN.
TOR does not keep any history or browsing session and relies on anonymity, but what about protecting s from malicious sites and software? Contrary to what one might imagine, TOR does not activate the protection module against misleading and dangerous content by default.

Even if this feature is enabled, the remains more exposed than on a browser such as Chrome or Firefox with regard to anti-phishing protection. Caution should therefore be exercised if you use TOR as your main browser.
TOR is transparent. On the source project blog are detailed all information about the browser’s , however, in 2018 several documents concerning the financing of the project leaked. It is reported that TOR has received several funds from US government agencies.
Our opinion on TOR 1702n
TOR is undoubtedly the most effective browser in of privacy protection. While the software is clearly not the most intuitive browser, it remains accessible. Developers have managed to find the right balance between security and convenience over the years, including providing a slider to adjust the level of security of TOR. Moreover, most of the program’s defects (slowness on some pages, poorly displayed content, lack of a ) are not really defects because they are an additional protection.
Rédigé par : The Logithèque Editorial Board

